VBO365: Create Azure AD applications automatically with least priviliges
Why?
As I am working with enterprises on my job I often hear they want to introduce a least privilege model for taking their Office 365 (I know, it’s Microsoft 365 – I’ll still use O365 anyways) backups.
While the product is of course capable of delivering a least privilege approach and documents all the required Azure AD permissions, the automatismn in the product uses a simpler approach which is good for 80-90% of the customers.
So the situation I am often facing: The admin responsible for taking O365 backup is no global admin in Azure AD, therefore he can’t use automatic app generation from within VBO.
The department responsible for the AzureAD (and/or security) will create an application based on the requirements to use in VBO.
And that’s exactly the point I am adressing here. Creating these applications by hand in a different appartment from the documentation can work good, but mostly there is something missing or misconfigured and you have to go back and forth. With tight schedules that easily can take up to some weeks and delay planned PoC schedules, etc.
What?
I am introducing a PowerShell script which helps to create the required Azure AD application (in the Azure AD). It generates a key-pair to use for authentication, creates the application and provides it with the required permissions for the usage type and services you’ve chosen. The Azure AD admin has then only to confirm the given permissions in the Azure AD portal and give the application ID and the key-file to the VBO admin for use in VBO authentication.
How?
Firstly, download the script from Github. Latest version in master will normally be the best choice: vbo-create-azure-ad-app.ps1
To run the script you’ll need the AzureAD PowerShell module installed. You can easily get it from PowerShell Gallery:
Install-Module -Name AzureAD
Please note that you can run this script from any computer with an internet connection. There is no dependency on any Veeam component in here.
Now you can run the script. To get some online-help you can run the Get-Help command on it to get a list of parameters, description, etc. With the -Detailed flag you can also get a description of every parameter:
PS> Get-Help .\vbo-create-azure-ad-app.ps1 -Detailed
NAME
D:\dev\veeam\backup_for_office365\vbo-create-azure-ad-app.ps1
SYNOPSIS
Create an Azure AD application for authentication, backup and recovery from Veeam's Backup for Microsoft Office 365
SYNTAX
D:\dev\veeam\backup_for_office365\vbo-create-azure-ad-app.ps1 -azureTenantId <String> [-appName <String>] [-limitUsageTo <String>] [-limitServiceTo <String[]>] [-certificateFilePath <String>] [-keyFilePath <String>] [-keyLifeTimeDays <Int32>] [-keyPassword
<SecureString>] [-overwriteKey] [-overwriteApp] [-azureAdCredential <PSCredential>] [-keyLength <Int32>] [<CommonParameters>]
DESCRIPTION
This script is meant to be used by a security or Azure AD administrator to provide the necessary Azure AD application to be used in Veeam Backup for Microsoft Office 365.
Use this script only if you can't use the product's built-in functionality to create the application (which will require Global Admin permissions).
The script will do the following and does not require any Veeam component to run:
1. Connect to Azure AD with given admin credentials
2. Create a public/private key-pair for app authentication and export the key to a file
3. Create a new application registration within Azure AD
4. Add the key for authentication to the app
5. Assign the required permisisons for VBO to the application
For a detailed list of permissions used in this script, please check
https://helpcenter.veeam.com/docs/vbo365/guide/azure_ad_applications.html?ver=50
The "Exchange/full_access_as_user" permission will not be created automatically - it is only required when the Office 365 region is "Germany" and would require special care in automation.
Based on limitations in the AzureAD powershell module the application can't be tagged as a public client when not limiting it to interactive restores. This step has to be done manually, but the script will inform at the end about it.
Created for Veeam Backup for Microsoft Office 365 v5
PARAMETERS
-azureTenantId <String>
Azure Tenant ID - can be found on the Azure AD overview page
-appName <String>
DisplayName for the app registration
-limitUsageTo <String>
Limit permissions to only those required for backup, InteractiveRestore (device authentication flow, e.g. Explorers) or ProgrammaticRestore (REST API-only), omitting this creates permissions for all usage types
-limitServiceTo <String[]>
Limit permissions to the following service(s). Omitting this creates permissions for all supported.
-certificateFilePath <String>
Path to the file where the public key will be stored (CRT)
-keyFilePath <String>
Path to the file where the private key will be exported (PFX)
-keyLifeTimeDays <Int32>
Lifetime of the key-pair in days
-keyPassword <SecureString>
Password for exported key file
-overwriteKey [<SwitchParameter>]
Overwrite/regenerate authentication key if exists
-overwriteApp [<SwitchParameter>]
Overwrite/regenerate app registration if exists with same name
-azureAdCredential <PSCredential>
Use the following credentials to connect to the Azure AD instead of asking. Can't be used for MFA
-keyLength <Int32>
Keylength for generated RSA key pair
Now with this information at hand you can run the script with the correct parameters to create applications in Azure AD.
Example Application Creation
Let’s run a simple example. You want different applications for backup and restore. You are using all services in your account.
First, let’s create a new Azure AD application for backup.
You need the Azure Active Directory ID (Tenant ID) to run the script. It’s required for the AzureAD connection.
To get this ID, head over to https://portal.azure.com with your Global Admin credentials.
When clicking on the “Azure Active Directory” view you can find (and copy) this information directly from the overview page:
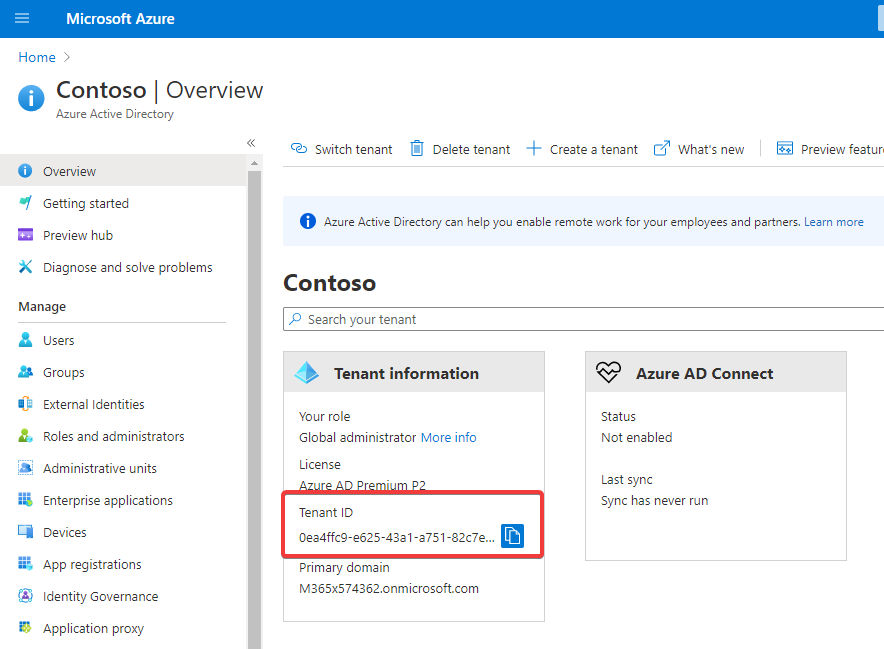
With this AD and the Global Admin credentials you can run the script. When entering parameters you will notice that there are some with tab auto-completion, like the -limitUsageTo, which has only three allowed values which will cycle through when hitting the tab key.
Let’s run the following command. All parameters but the -azureTenantId are optional:
PS> .\vbo-create-azure-ad-app.ps1 -azureTenantId 0ea4ffc9-e625-43a1-a751-82c7e35a9fba -limitUsageTo Backup -appName VBO_BACKUP_ONLY -certificateFilePath .\vbo_backup_only.crt -keyFilePath .\vbo_backup_only.pfx
The script wants to connect to the AzureAD and asks for credentials. Note that the cyan output of the script will always require interaction.
Log in with your Global Admin credentials here. The login form also supports MFA authentication.
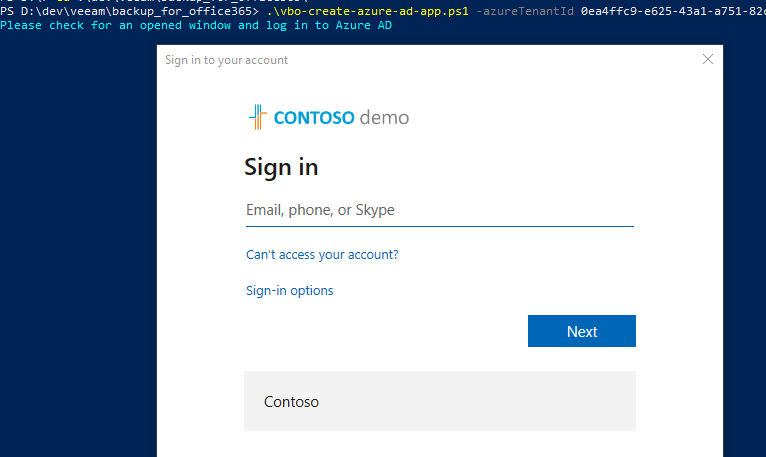
After the login the scripts asks you for a password to encrypt the exported key file and then will create the requested application and add this key for authentication:
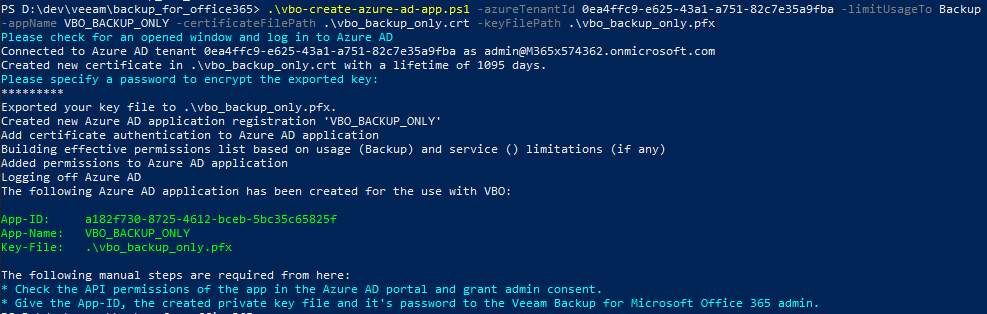
There are two more cyan call outs to you as the Global Admin. First, check the permissions in AzureAD and give admin consent – the following is an animated GIF showing this consent process:
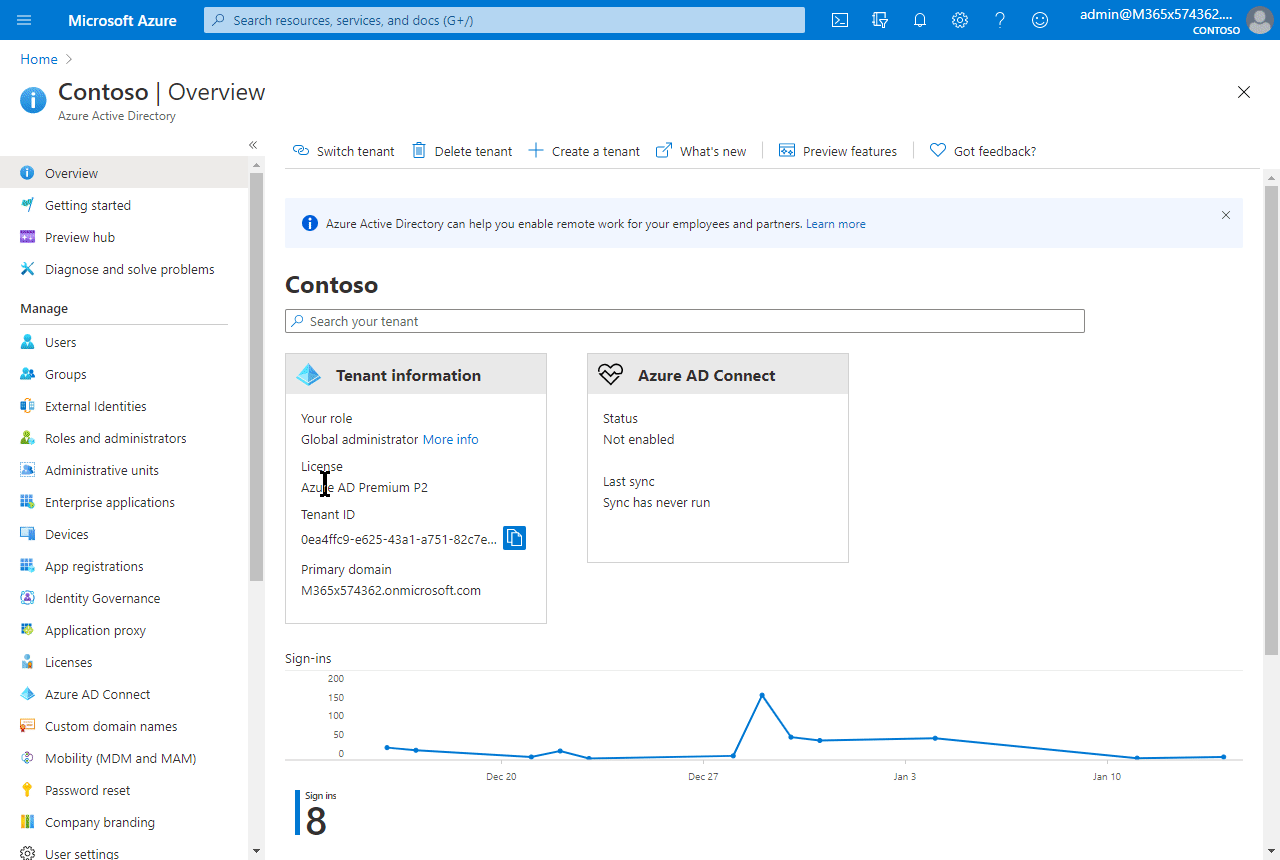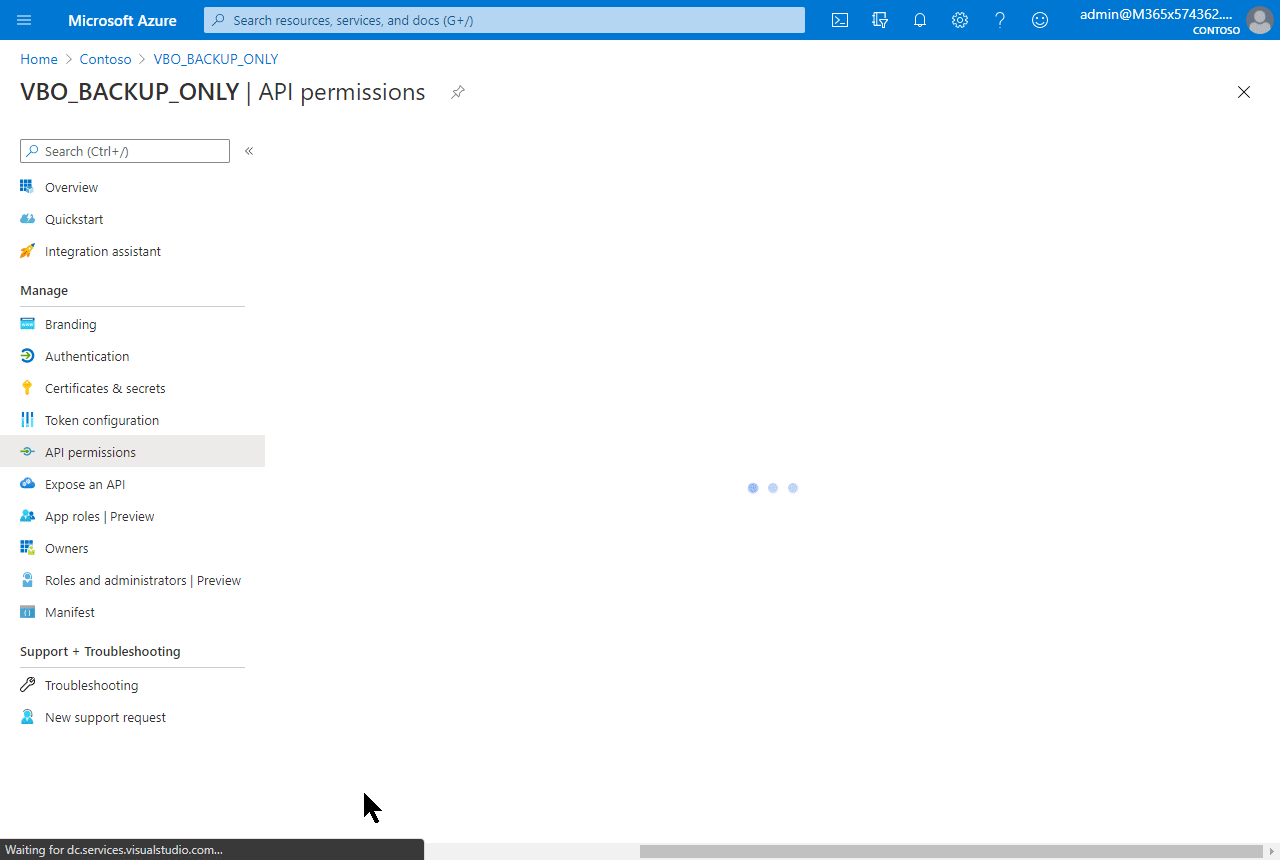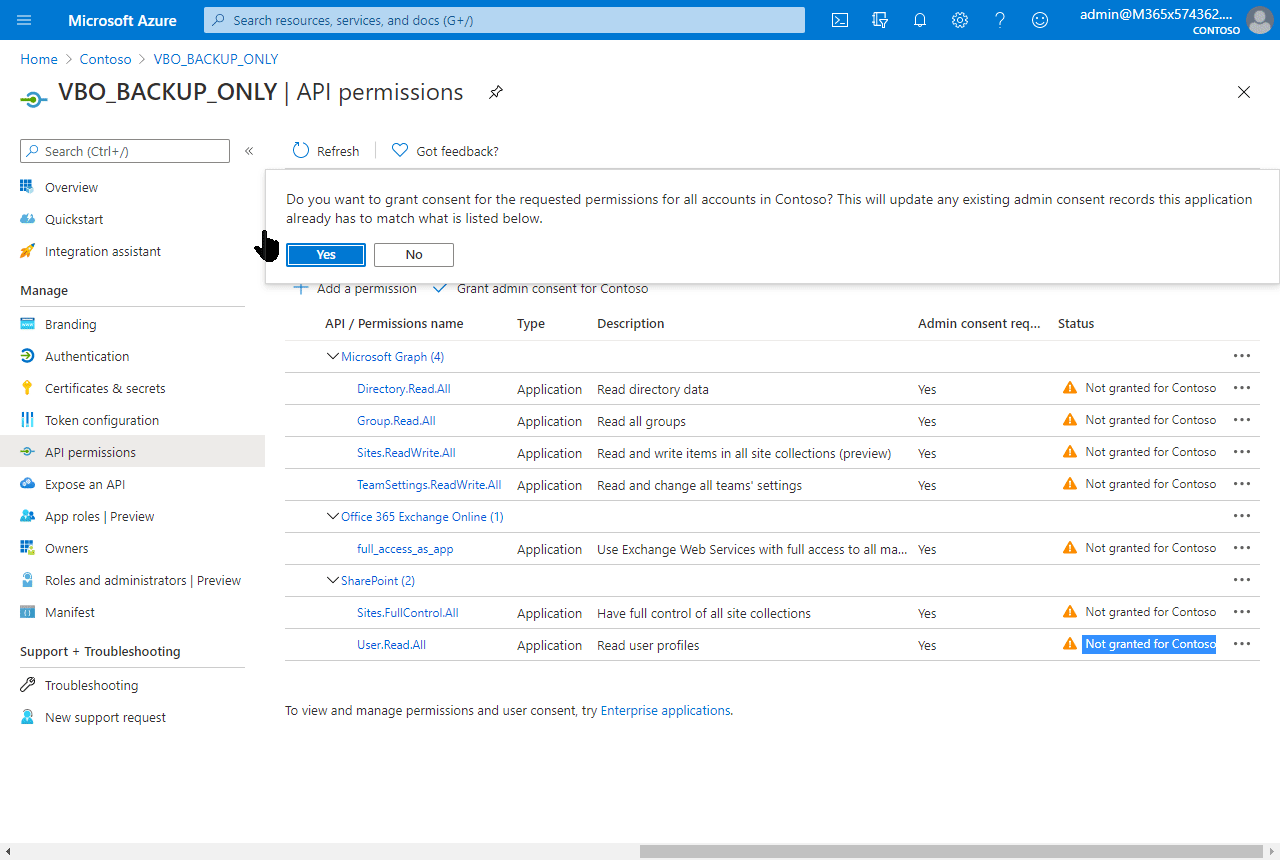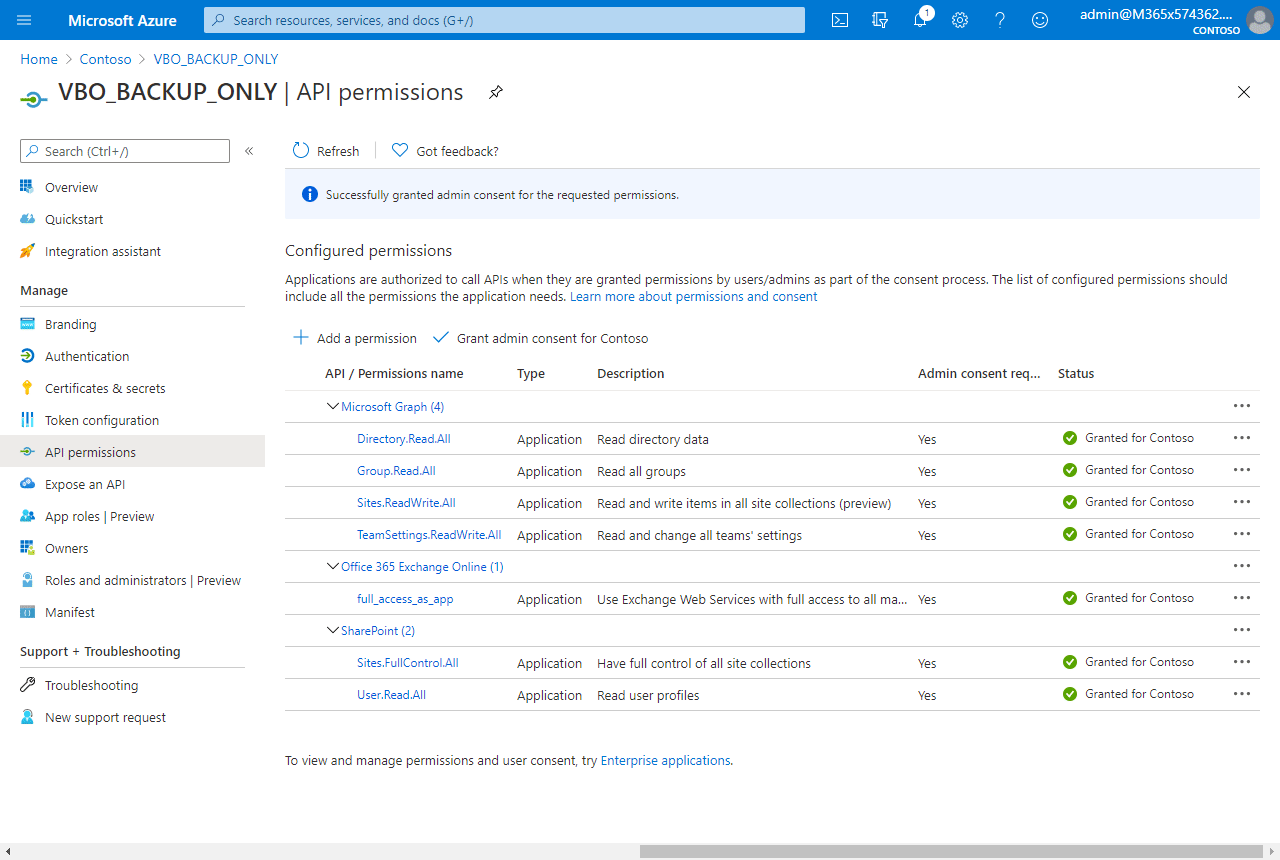
Now the application is all set for usage. Now the VBO admin will require three things to use it:
- The
vbo_backup_only.pfx(name can vary based on the –certificateFilePathparameter): This is the exported private key to use for authentication. - The password with which the PFX exported key was encrypted (chosen in the script run)
- The application ID, visisble in the script’s output (
a182f730-8725-4612-bceb-5bc35c65825fin the example) or in the Azure AD portal in the app registrations.
Caveats
Due to limitations in the AzureAD module and/or Azure AD API there is another requirement for manual action when including the interactiveRestore permission type. You will have to enable the “Allow public client flows” setting for the app manually via the Azure AD portal. The script will, however, notify you about that when it’s required.
What’s next?
Have a look at the following posts and look out for more to come:
One Reply to “VBO365: Create Azure AD applications automatically with least priviliges”
Comments are closed.